At every available opportunity, I partake in airborne WiFi services. Yeah, I know public wireless isn’t the most secure form of connectivity. But, at the same time, I haven’t been bothered to set up a personal tunnel. And I’ll do just about anything to pass the time on a cross country flight… as I did when returning from CES last week. Southwest’s wireless service runs a mere $5 during testing and linking up on my LAS>BWI flight (3140, 1/8) was a no brainer – especially as I hadn’t loaded up my iPhone with content and my Kindle was left at home.
Unfortunately, there’s something not quite right with their Internet connection in relation to Twitter. As you can see, I wasn’t the only one in my account:
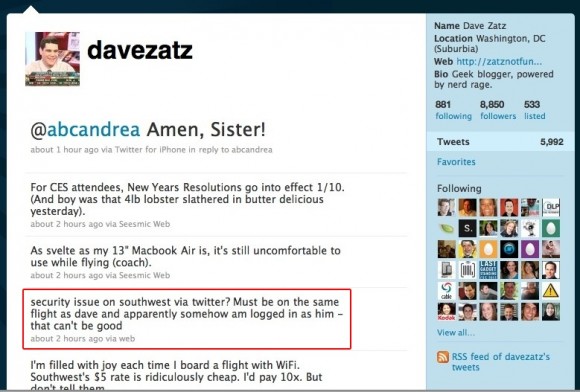
The interloper acted in the same manner I would have. Not entirely benign, but mostly benevolent as far as I can tell by merely firing off that lone alert. I’m not so concerned about anything in my archived Twitter direct messages, as it’s mostly boring stuff. I operate under the assumption that everything/anything online can become public at any time. Internet privacy is an easily shattered illusion.
Now it’s possible this person swiped my credentials off the network using something like Firesheep. But I’d expect a person dabbling in such affairs to more proudly proclaim I’d been p0wned. Followed by additional mayhem. So I’m taking him/her at face value and suspect somehow the packets were unintentionally crossed. And at the time there was super high latency on the network. Combined with Southwest’s proxy and framing of every web page (see below, left), I guess anything is possible. Although it shouldn’t be.
At the time of discovery, two hours after the fact, I was obviously startled and the only action I came up with was to delete the tweet. In retrospect, I should have left it be so as to not impact any possible forensic research. And to provide a more compelling post. But the screen grab will have to suffice. Once I deplaned, I changed my unique Twitter password, as a precaution, via aircard.
So consider this post a public WiFi PSA in addition to a security vulnerability notification to Southwest and Twitter. I’ll provide updates if either of them choose to respond.
(Thanks for alerting me, Steve!)
This is probably a caching issue with the software the plane is using to optimize data transmission. Something similar occurred a few years ago with a cellular carrier where its caching servers were mixing up session data and allowing people access to the wrong facebook accounts.
If the service keeps everything SSL encrypted (HTTPS for all content), this can be avoided, as would have using a VPN.
Wow, I thought you were kidding around when I saw that Tweet. Though, at the time, I admit I didn’t get it.
JeffS, yeah I wish more/all sites used https across the board (and not just a portion of a login screen).
Robs67, you’re not alone. When I asked my wife why she didn’t alert me (from the ground), she said she didn’t understand what I was trying to convey with that tweet. Of course, *I* wasn’t trying to convey anything. Heh.
Things like this are one reason why I installed KB SSL Enforcer in Chrome and HTTPS Everywhere in Firefox (even though I really don’t use it anymore, just in case). I wish more applications could be forced to use SSL.